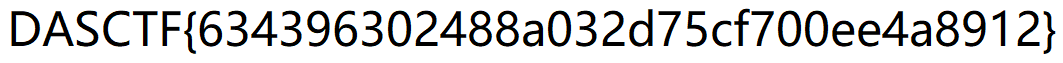Misc Justpainting 010打开压缩包,发现结尾多了五个?,猜测加密压缩包的密码是五位
爆破得到密码11452
打开得到一个python脚本和一张jbn.pth
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 import torchimport torch.nn as nnimport numpy as npimport matplotlib.pyplot as pltfrom PIL import Imageimport cv2class JBN (nn.Module):def __init__ (self ):super (JBN, self).__init__()100 , 256 ),256 , 512 ),512 , 452 * 280 ),def forward (self, x ):1 , 452 , 280 )return imgdef watch_flag (img ):'./data/data/flag.png' )0 ).transpose(1 , 2 )0 )0 )float (), img_tensor)return loss0.001 )float ('inf' )for epoch in range (10 ):1 , 100 )with torch.no_grad():if g_loss < min_loss:'jbn.pth' )
题目的意思很明确,根据源码和jbn.pth反向生成flag
chatgpt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 import torchimport torch.nn as nnimport numpy as npimport matplotlib.pyplot as pltfrom PIL import Imageimport cv2class JBN (nn.Module):def __init__ (self ):super (JBN, self).__init__()100 , 256 ),256 , 512 ),512 , 452 * 280 ),def forward (self, x ):1 , 452 , 280 )return imgdef generate_flag (jbn_model, output_path ):eval ()with torch.no_grad():1 , 100 )1 ) / 2 0 , 1 ) 'gray' )'off' )'tight' , pad_inches=0 ) 'jbn.pth' , 'generated_flag.png' )
justlisten 扫描汉信码hint.png,得到
010打开this is our secret.bmp
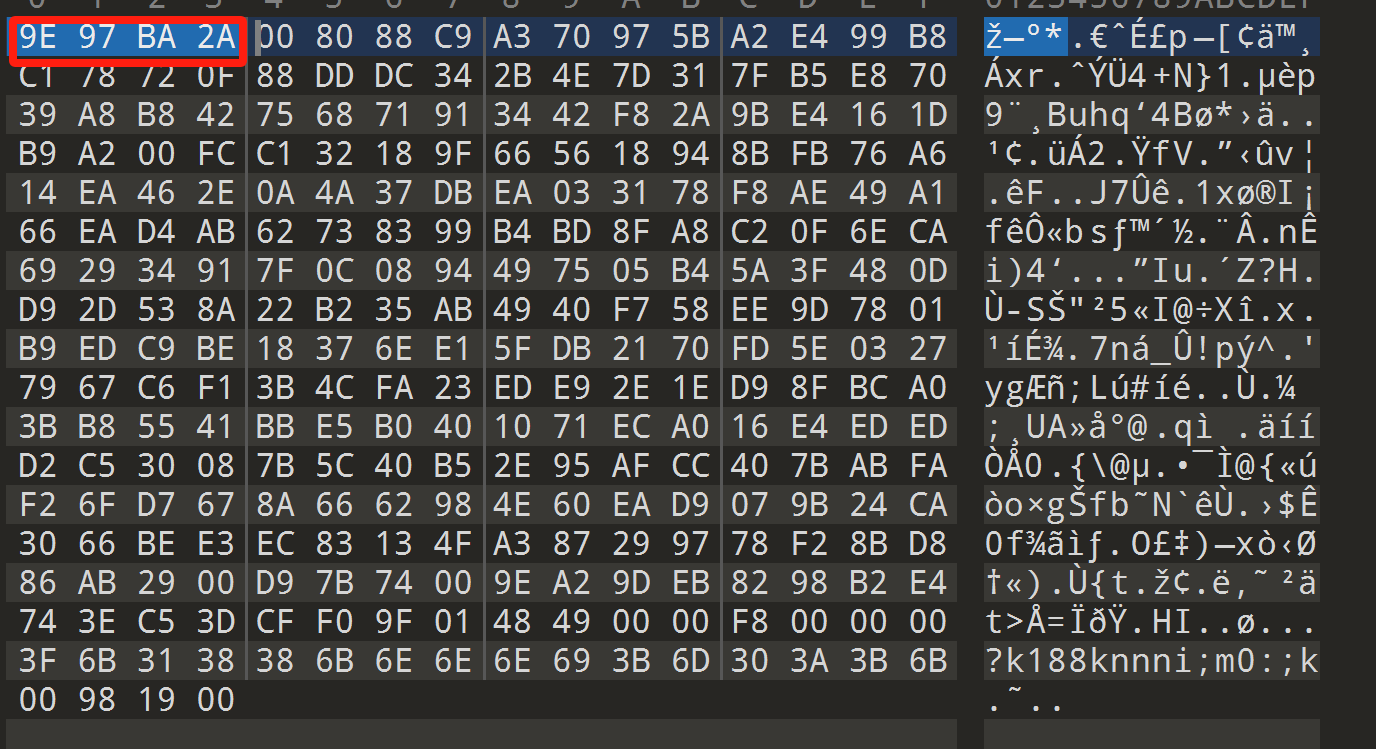
9e97ba2a是oursecret的特征
使用oursecret对bmp文件进行提取,密码是0urS3cret
提取出一个haha.txt
1 abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_}{-?!
应该是一个字典
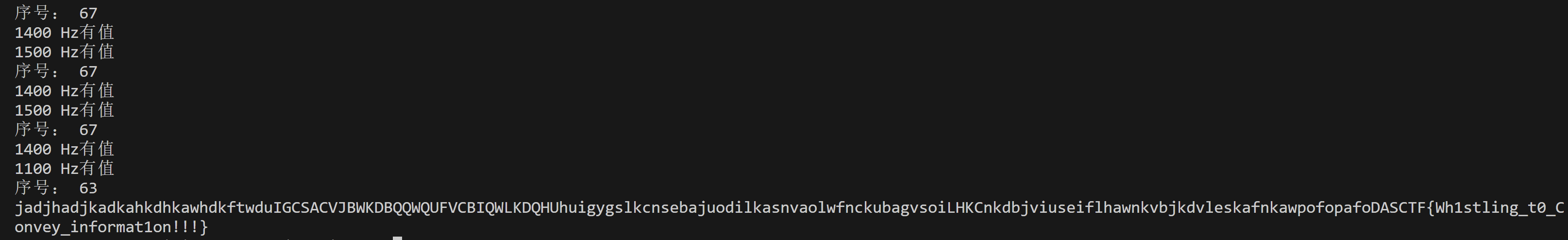
用Audacity查看嘘.wav文件,看它的频谱图,得知它的频率为[800,900,1000,1100,1200,1300,1400,1500,1700,1800]以及它的每个频率变化的时间为0.1s,同时可以得知它的采样频率为44100
脚本读取wav文件的数据长度
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 import numpy as npimport waveimport scipy.fftpack as fftpack44100 0.1 int (SAMPLE_RATE * SAMPLE_TIME) 800 , 900 , 1000 , 1100 , 1200 , 1300 , 1400 , 1500 , 1600 , 1700 ]with wave.open ('嘘.wav' , 'rb' ) as f: 1 ), dtype=np.int16)len (wav_data) print (N) 44100 *0.1 ))/189 print (a)
可以得知数据长度N=1666980,然后再a = (N/(44100*0.1))/42来计算每个字符占了多少时长为0.2s
处理一下数字信号,并根据分离出的字典来获取隐藏的数据
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 import numpy as npimport waveimport scipy.fftpack as fftpack44100 0.1 int (SAMPLE_RATE * SAMPLE_TIME) 800 , 900 , 1000 , 1100 , 1200 , 1300 , 1400 , 1500 , 1600 , 1700 ] def fft (data ):len (data) abs (fft_data) 2 ) range (N//2 )] return half_fftdef dec_100ms (wave_data_100_ms ): for index, freq in enumerate (LIST):if np.max (fft_ret[int (freq*SAMPLE_TIME) - 2 : int (freq*SAMPLE_TIME) + 2 ]) > 0.8 :print (freq, 'Hz有值' )return indexdef dec_sentence (wav_data ): len (wav_data) // SAMPLE_NUM print ('待解码音频包含' , _100ms_count // 2 , '个字' ) '' for i in range (0 , _100ms_count, 2 ): 0 for k in range (2 ):10 + dec_100ms(wav_data[i*SAMPLE_NUM + k*SAMPLE_NUM : i*SAMPLE_NUM + (k+1 )*SAMPLE_NUM])print ('序号:' , index)return retif __name__ == '__main__' :with open ('haha.txt' , 'r' , encoding='utf8' ) as f:with wave.open ('嘘.wav' , 'rb' ) as f: 1 ), dtype=np.int16)print (dec_sentence(wav_data))
运行得到flag
NoPasswd 打开doc文件发现加密
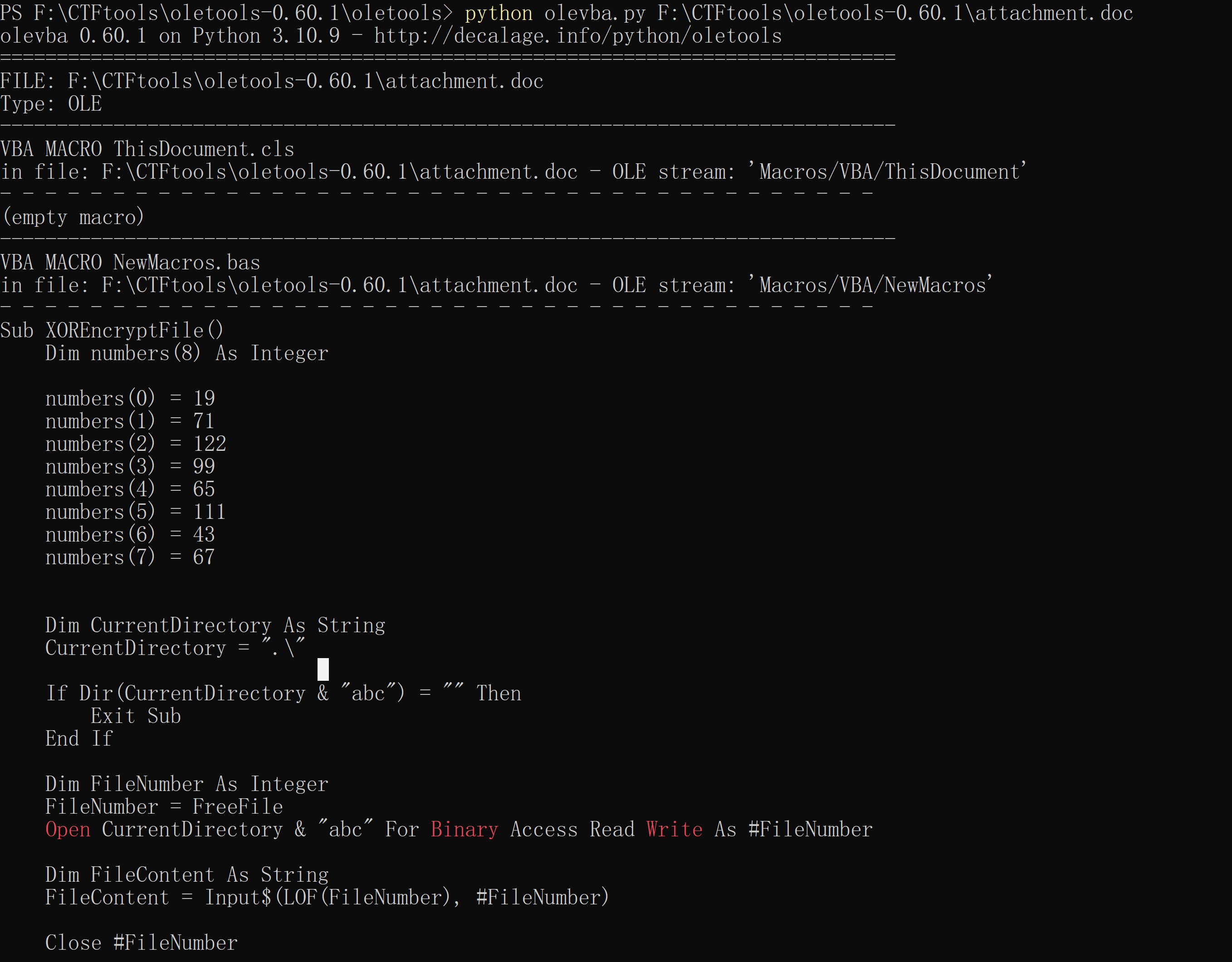
查看属性发现宏孩儿和60290f0225011a72697f420d1f4e402778231b
1 2 3 4 5 6 7 oleid:分析OLE文件以检测通常在恶意文件中发现的特定特征。MS Office 文档(OLE和OpenXML)中提取和分析VBA Macro源代码。MS Office 文档,RTF和CSV中提取DDE / DDEAUTO链接MS Office 文档(例如Word,Excel)和RTF等文件中的Flash对象(SWF),这对于恶意软件分析特别有用。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 Sub XOREncryptFile()Dim numbers(8 ) As Integer 0 ) = 19 1 ) = 71 2 ) = 122 3 ) = 99 4 ) = 65 5 ) = 111 6 ) = 43 7 ) = 67 Dim CurrentDirectory As String ".\" If Dir(CurrentDirectory & "abc" ) = "" Then Exit Sub End If Dim FileNumber As Integer "abc" For Binary Access Read Write As #FileNumberDim FileContent As String Dim EncryptedContent As String For i = 1 To Len(FileContent)Mid (FileContent, i, 1 )) Xor numbers((i - 1 ) Mod 8 ))Next i"enc" For Binary Access Write As #FileNumberEnd Sub
分析一下可以知道就是简单的异或,enc应该就是备注中的16进制字符串,写个脚本解密一下可以得到doc的密码,解开doc可以发现base64字符串,解码一下可知是zip文件
1 2 3 4 5 6 7 8 9 10 11 from Crypto.Util.number import *0x60290f0225011a72697f420d1f4e402778231b )19 ,71 ,122 ,99 ,65 ,111 ,43 ,67 ]"" for i in range (len (enc)):chr (enc[i] ^ key[i%8 ])print (abc)
解密得到一堆文字,可能是base64,cyberchef解密发现是zip,导出压缩包发现是伪加密
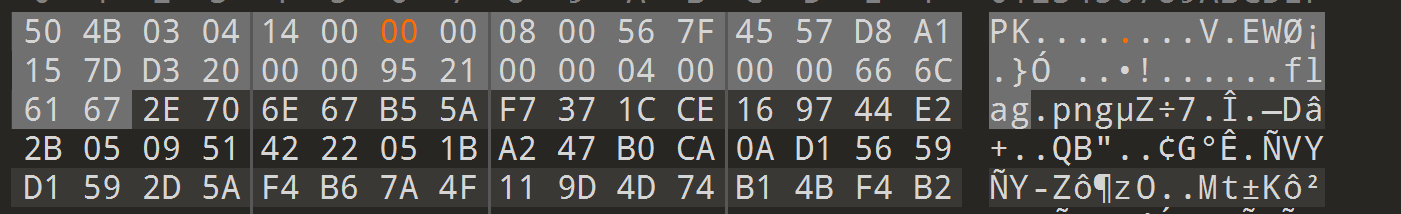
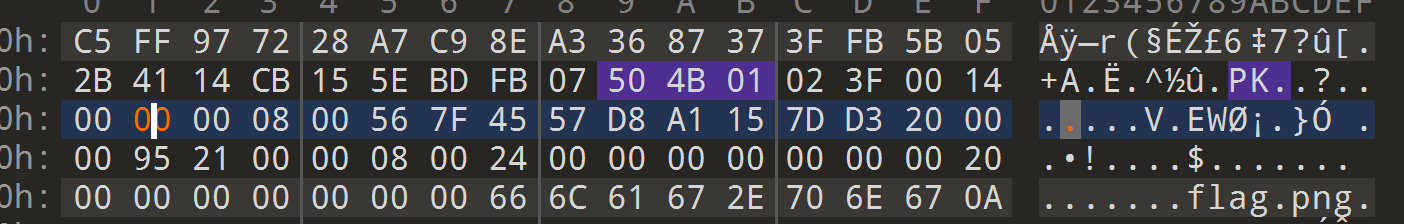
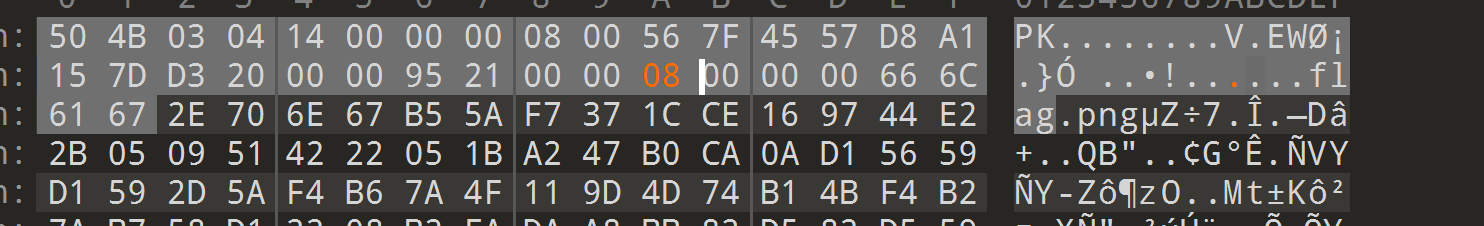
解压缩发现报png文件格式错误,说明压缩包里的是png,我们看看变量的数据
发现文件名应该是flag.png一共8个字节,但是变量那边的name长度只有4个字节,所以我们要改成8个字节
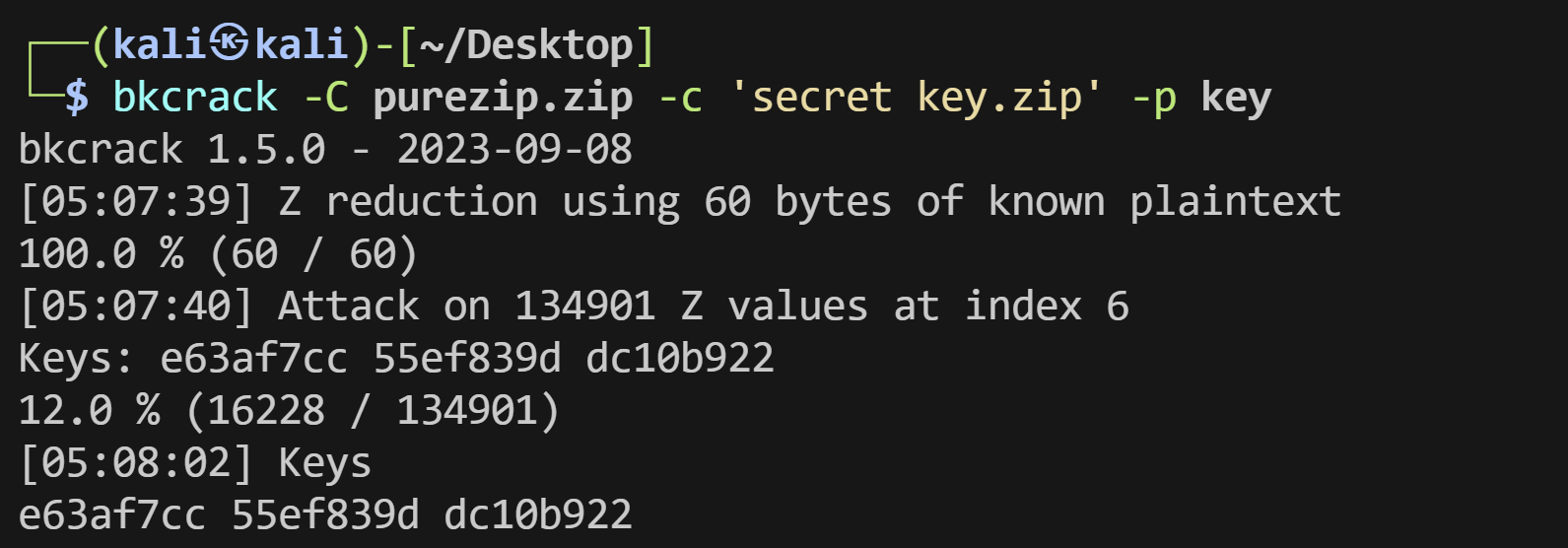
SecretZip 题目给了一个key文件,以及一个加密的zip,key文件内其实是压缩包明文压缩后的前半部分,因此压缩包虽然不是store的压缩模式,也能进行已知部分明文攻击
1 bkcrack -C purezip.zip -c 'secret key.zip' -p key
1 e63af7cc 55 ef839d dc10b922
解密的数据可能会被压缩,具体取决于创建 zip 文件时是否使用压缩。如果使用 deflate 压缩,则tools可以使用文件夹中提供的 Python 3 脚本来解压缩数据。
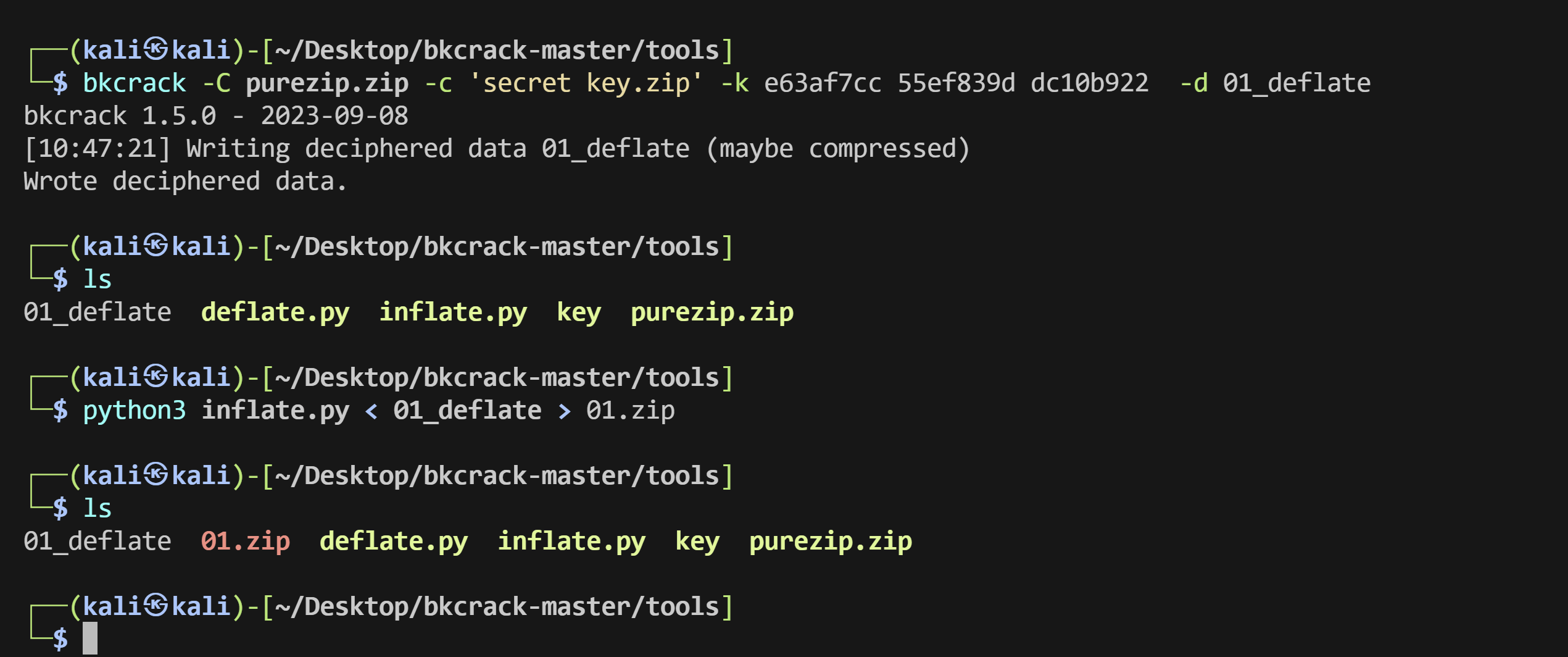
1 2 bkcrack -C purezip.zip -c 'secret key.zip' -k e63af7cc 55 ef839d dc10b922 -d 01 _deflatepython3 inflate.py < 01 _deflate > 01 .zip
01.zip在010查看发现提示密码是2字节
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 import zipfileimport libnumfrom tqdm import trangefor i in trange(256 ):for j in range (256 ):'01.zip' , 'r' )try :print (password)break except :continue else :continue break
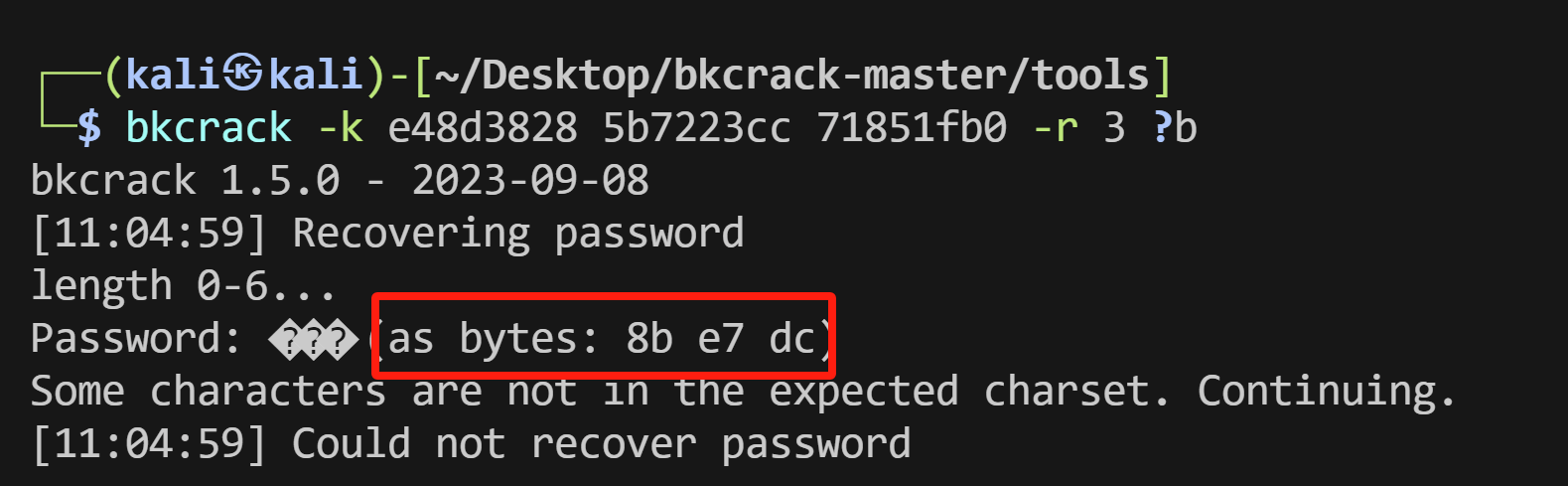
解压出一个secret key.txt,里面内容e48d3828 5b7223cc 71851fb0
同时在zpaq文件的文件尾得到提示the password is md5(the plaintext of the secret key which length is 3 bytes)
因此要还原pkzip的三段秘钥,但是发现bkcrack自带了秘钥还原的接口
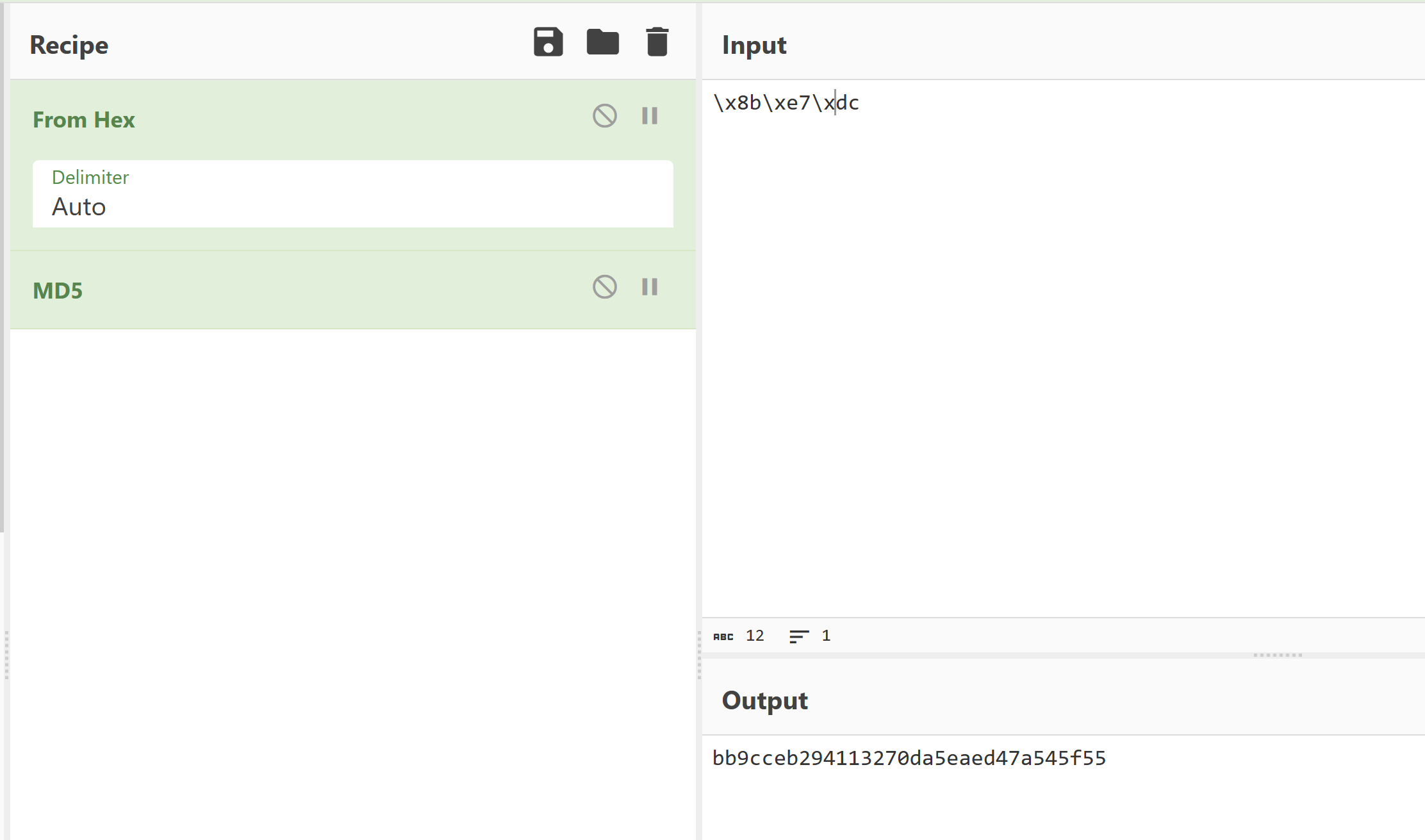
1 bb9cceb294113270da5eaed47a545f55
解压得到flag